SCHNEIDER Quantum Safety PLC: Complete Analysis of SIL3 Safety Control System
Schneider Electric Quantum Safety PLC: A High Reliability Safety Control System for SIL3 Applications
1. Product Overview and Certification Background
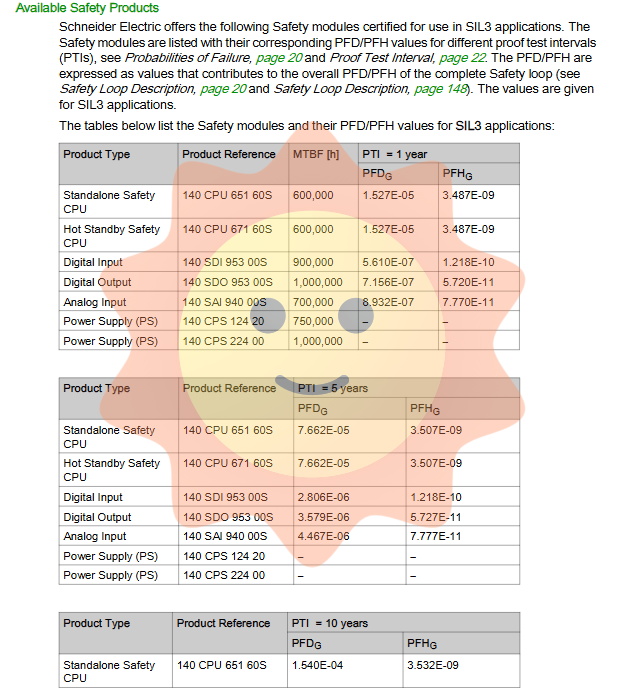
Quantum Safety PLC is a safety related system developed by Schneider Electric based on the Quantum series programmable logic controller (PLC), specifically designed to meet the functional safety requirements of IEC 61508 standard. This system is certified by T Ü V Rheinland and supports applications up to SIL3, suitable for safety scenarios in low demand mode (PFD ≥ 10 ⁻⁴ to<10 ⁻³) and high demand mode (PFH ≥ 10 ⁻⁸ to<10 ⁻⁷). Its safety state is defined as the de energized state, which is typically applied to critical industrial processes such as emergency shutdown, burner management, fire protection, and gas systems.
In addition to IEC 61508, this PLC also complies with multiple international and industry standards such as IEC 61131-2, IEC 62061, EN ISO 13849, NFPA 85/86, EN 54, and EN 298, and has a wide range of applicability. The system must use certified security firmware and Unity Pro XLS programming software to ensure full chain security compliance from hardware to software.
2. Hardware architecture and security mechanisms
2.1 Secure CPU and Dual Execution Architecture
Quantum Safety PLC provides two types of safety CPUs:
140 CPU 651 60S: for standalone systems
140 CPU 671 60S: Used for Hot Standby high availability systems
The CPU adopts a dual processor architecture (Intel Pentium and application processor) internally, which executes the same security logic in independent memory areas and compares the results at the end of each cycle. This dual code generation and execution mechanism can effectively detect:
Systematic errors in code generation (through compiler diversity)
Systematic errors during code execution
Random errors in CPU and RAM
The CPU has built-in hardware and firmware watchdog to monitor PLC activity and user logic execution time. Static memory (Flash, PCMCIA card, RAM) is verified through cyclic redundancy check (CRC) and dual code execution; Dynamic memory is protected through dual code execution and periodic memory testing.
2.2 Safety I/O module
The system supports three types of certified secure I/O modules:
140 SAI 940 00S: Safety analog input (8 channels, 4-20 mA)
140 SDI 953 00S: Secure Digital Input
140 SDO 953 00S: Secure Digital Output
All safety I/O modules adopt a dual microcontroller system, running the same program and regularly cross checking. The module supports local backplane or remote I/O station installation, and communicates with the CPU through the "black channel" protocol to ensure that errors can be detected during data transmission. The module has comprehensive diagnostic functions, including wire breakage detection, overload, out of range, power monitoring, etc., and supports redundant configuration to improve availability (but redundancy does not enhance safety level).
2.3 Non interfering modules and power supply
The system allows the use of non-interference modules to expand non safety functions, such as:
Backboard (140 XBP 006/010/016 00)
Remote I/O adapter (140 CRP 932 00/140 CRA 932 00)
Ethernet module (140 NOE 771 11)
Standard digital/analog I/O module
These modules do not affect the execution of safety functions, and faults will not affect the safety modules. The power module (140 CPS 124 20/140 CPS 224 00) is certified but does not contribute PFD/PFH values. The system recommends equipping each rack with dual power supplies to achieve redundancy.
3. Programming and software requirements
3.1 Programming Environment and Language Limitations
Only Unity Pro XLS (XL Safety version) can be used for SIL3 project programming. This software provides project protection, self checking functions, and a library of security function blocks. Programming languages are limited to:
Function Block Diagram (FBD)
Ladder diagram (LD)
It is prohibited to use languages such as ST, IL, SFC, as well as subroutines, interrupt tasks, conditional segment execution, and jump labels. All security logic must be written in the MAST task segment.
3.2 Data and Memory Management
Memory is divided into safe memory area and unrestricted memory area (UMA):
Secure memory area: write protected, used for processing security related data
Unrestricted memory area: can be written, but data needs to be transferred to secure memory through the secure move function block (s_SMOVE-BIT/s_SMOVE_SWORD) before it can be used
Only basic data types (BOOL, INT, WORD, etc.) and simple arrays are allowed, and derived data types are prohibited. All variables must be located and their addresses must be within a valid memory range.
3.3 Safety Function Block Library
Unity Pro XLS provides a certified library of security feature blocks, covering functions such as mathematical operations, comparison, logic, statistics, timers, type conversion, high availability, and hot standby. The key functional blocks include:
S-AISIL2/S-DISIL2: Used for selecting and monitoring redundant analog/digital inputs
S-HSBY_SWAP: Used for switching between primary and backup CPUs in hot standby systems
S-WR-ETH/S-RD-ETH: Used for secure Ethernet peer-to-peer communication
4. Operation mode and diagnosis
4.1 Security Mode and Maintenance Mode
Safe mode: default mode, prohibited from modification and maintenance, only allowed to start and stop PLC. All safety functions are activated and the diagnostic results have been fully evaluated.
Maintenance mode: used for debugging, forcing values, and modifying programs. The diagnosis is still running but the results have not been fully evaluated. The mandatory value remains unchanged when switching to safe mode.
Mode switching needs to be controlled through a key switch, Unity Pro XLS, or CPU keyboard. Modifications made in maintenance mode must comply with the requirements of IEC 61508 and refer to T Ü V's "Maintenance Override" document.
4.2 Diagnosis and Error Handling
The system has multi-level diagnosis:
CPU diagnosis: dual processor comparison, memory check, watchdog monitoring
I/O diagnosis: channel health status, communication CRC check, power monitoring
Communication diagnosis: Black channel protocol detects transmission errors, omissions, disguises, etc
Once an error is detected, the system behavior varies depending on the pattern:
In safe mode: enter error state, all safe outputs enter safe state
In maintenance mode: entering the shutdown state, communication and debugging can still be carried out
The error information is stored in the system words% SW125-% SW127 for subsequent analysis. When the I/O module fails, only the faulty channel enters a safe state, while the other channels continue to operate.
5. Communication Security and Network Integration
5.1 Secure Ethernet Peer to Peer Communication
By configuring NTP service, S-WR-ETH/S-RD-ETH function block, and IO scanning service, SIL3 level secure communication between PLCs can be achieved. This communication is based on a black channel mechanism, which can detect and manage transmission errors, delays, address errors, etc. All Ethernet devices (switches, NTP servers) do not contribute PFD/PFH values.
5.2 Write Protection and Memory Isolation
The secure memory area provides write protection for external devices such as HMI and other PLCs. The unrestricted memory area can receive external data, but it must be transferred to secure memory through the secure move function block before it can be used for secure logic. Unity Pro XLS checks this rule during editing and building to ensure data flow isolation.
5.3 Communication Restrictions
Do not use Ethernet or Modbus Plus to connect I/O modules
Prohibit the use of distributed I/O or fieldbus I/O
Allow Ethernet/Modbus Plus to be used for communication between PLCs or PLC-HMI, but read can only be for unlimited memory areas
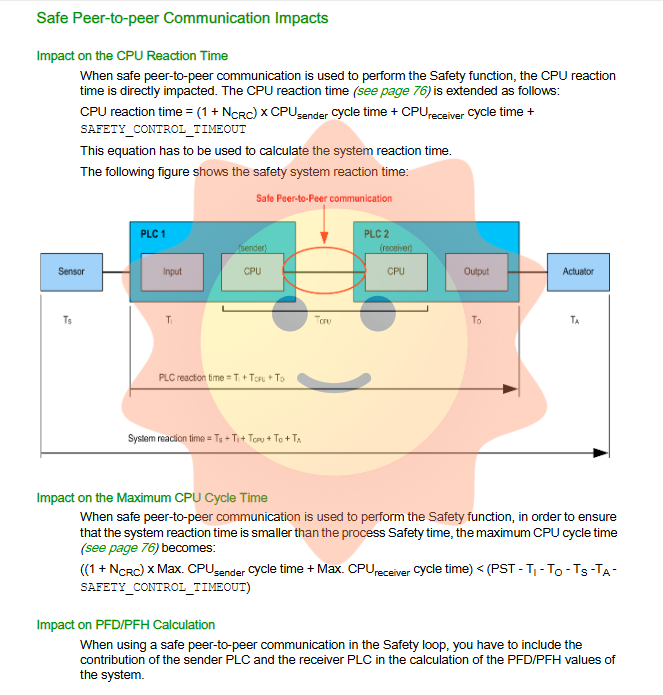
6. Safety time and performance calculation
6.1 Process Safety Time (PST) and System Response Time
PST refers to the time window from the occurrence of equipment failure to the occurrence of hazardous events. The system response time must be less than PST, and its calculation formula is:
System response time=PLC response time+sensor time+actuator time
PLC response time=CPU response time+input module time+output module time
CPU response time=(2+N_CRC) x CPU cycle time
Among them, N_CRC is the maximum allowed number of consecutive CRC errors (1-3).
6.2 Maximum CPU cycle time calculation
When considering secure peer-to-peer communication, the maximum CPU cycle time must meet:
(1+N_CRC) x Max (CPU-sender cycle time)+Max (CPU-receiver cycle time)<PST - ∑ each link time
The timeout of the output module must be greater than the CPU cycle time to ensure that the safe state can be triggered in a timely manner in case of failure.
7. Configuration List and Implementation Suggestions
The manual provides multiple checklists covering configuration, programming, I/O modules, secure peer-to-peer communication, and operation and maintenance. Key recommendations include:
Use authenticated security and non-interference modules
Each rack is equipped with dual power supplies
Redundant I/O modules should be distributed in different remote stations
Enable all warning options during programming and review them one by one
Regularly backup projects and test recovery processes
Follow T Ü V documentation for maintenance and mandatory operations
8. Industry specific requirements
8.1 Fire and Gas System
Must comply with EN 54 standard, requirements:
Detect open/short circuits in the circuit and sound an alarm
power redundancy
Analog input requires monitoring of ground faults (leakage current), usually achieved through shunt resistors and grounding devices
8.2 Emergency Shutdown and Burner Management
The safety status is in power-off state. The burner system must comply with EN 298, ensuring that the entire time from detection to safe shutdown does not exceed 1 second, and the on-site power supply must be a 20-25 VDC regulated power supply.
- ABB
- General Electric
- EMERSON
- Honeywell
- HIMA
- ALSTOM
- Rolls-Royce
- MOTOROLA
- Rockwell
- Siemens
- Woodward
- YOKOGAWA
- FOXBORO
- KOLLMORGEN
- MOOG
- KB
- YAMAHA
- BENDER
- TEKTRONIX
- Westinghouse
- AMAT
- AB
- XYCOM
- Yaskawa
- B&R
- Schneider
- Kongsberg
- NI
- WATLOW
- ProSoft
- SEW
- ADVANCED
- Reliance
- TRICONEX
- METSO
- MAN
- Advantest
- STUDER
- KONGSBERG
- DANAHER MOTION
- Bently
- Galil
- EATON
- MOLEX
- DEIF
- B&W
- ZYGO
- Aerotech
- DANFOSS
- Beijer
- Moxa
- Rexroth
- Johnson
- WAGO
- TOSHIBA
- BMCM
- SMC
- HITACHI
- HIRSCHMANN
- Application field
- XP POWER
- CTI
- TRICON
- STOBER
- Thinklogical
- Horner Automation
- Meggitt
- Fanuc
- Baldor
- SHINKAWA
- Other Brands